By Yoon Auh, Founder of NUTS Technologies, August 27th, 2022.
The Internet of Data™ (IoD™) enables direct access to data across any network. Accessing data directly is possible when data has at least two characteristics: identification and privacy.
Identification of Data
Identification of objects is conventionally implemented within narrow scopes such as VIN, SSN, cell number, MEID, MAC, IPv4, IPv6, etc. For IoD, any data is eligible for permanent identification using a Practically Unique ID (PUID) by any capable device.
Identification of data is as narrow or broad as required and easily implemented with an identifier: the larger the identifier, the bigger the possible universe of data. A large enough identifier can identify the data across space and time. The size of the data identifier can start small and grow as needed; as implemented, this identifier is defined as the NutID. NutIDs are unstructured identifiers to maximize anonymity; this has the implied consequence of making brute force guesses very expensive for an identifier to a piece of data.
Privacy of Data
Privacy of data is conventionally controlled through access gateways and obfuscations (ciphering), each of which present numerous technical challenges when done at scale. To secure data for IoD, it is convenient to have a compact, fine grained, access control system that is cryptologically implemented as data; we define data secured by a compact, independent, portable access control system as Zero Trust Data (ZTD). Other equivalent terms for ZTD are “Secure Container” and “Security at the Data Layer”.
A Secure Container implemented as an encapsulation can be used to envelope the payload to accommodate a wide variety of object and file formats. Within the secure container, any metadata is also protected (immutable).
We define a simple nut container as a secure container with an immutable NutID as metadata and the data to be protected as the payload where the access controls are expressed as sets of cryptographic keys configured into progressively revealing data structures.
Thus, data in a nut can be accessed directly by any key holder(s) on the Internet of Data.
Independent Data
Data in a nut is independent data. An IoD ecosystem can provide transport and locate services for independent data across any network. The nut can be addressed directly by its NutID, further, the nut can address other nuts by their respective NutIDs; therefore, a NutID is a permanent reference to a nut in contrast to impermanent URL paths. In essence, the secure container protects and identifies its payload. A nut with a payload of NutIDs is an example of data directly addressing other data.
It is nontrivial to store and forward URLs by other web servers, whereas a nut can be handled by any relay mechanism due to its intrinsic security and portability. URIs and URLs are ever changing and may not be the same the next time you visit them. Documents not visible to web searches are very difficult to track down. Document authentication is even more difficult. In contrast, a NutID of a document will never change and references the actual document which will self-authenticate upon presentation of a valid key.
Independent data in a nut protects its payload and only the key holder(s) can easily access it; therefore, a nut can be safely stored anywhere on the IoD. Expressed as a generic file format such as JSON-base64, a nut is independent of most Operating Systems, File Systems and Cloud Systems. Getting a copy of a random nut is not enough to access its contents, one must present a valid credential in the form of cryptographic key. Since the access controls for the nut are embedded within its container material as cryptographic data elements, the payload is consistently protected in any environment independent of reference monitors.
Key Management
A secure system requires the safekeeping of secrets such as cryptographic keys in a systematic way on behalf of the user; a nontrivial problem. In the evolving world of data security, the ownership of cryptographic keys is an important factor in establishing the ownership of ciphered data. Both concerns can be addressed effectively and simply within a IoD implementation using nut containers.
IoD as implemented by the NUTS ecosystem provides each user installation with a key management system (KMS) built on nut containers. Since a nut identifies and protects a payload of any storable digital data, a cryptographic key or digital credential stored as payload in a nut is private and an identified in a universal way.
A nut container can be configured with an arbitrary number of keyholes each of which is identified by a NutID (or within this context, a KeyID). This presents the raw building blocks to construct a secure, robust and modular KMS using nuts as key carriers: a simple, elegant, logical and massively scalable design.
Conclusion
Our research shows that when properly engineered, IoD can provide an individual user with features often associated with the most sophisticated IT organizations such as hybrid cloud data management, data resiliency, ransomware mitigation, insider threat mitigation, automatic backup, hot backup, secure data sharing, automated synchronization, cipher agnostic cryptography, on device key management, and key ownership. All of these features in one ecosystem in an integrated fashion expressed as protected, identifiable data storage units.
Conventional approaches may provide most of the features listed above but may require many solutions to be configured simultaneously by knowledgeable people with integration as an secondary concern. Insider threat mitigation is only attempted by organizations with deep pockets and the need whereas the NUTS ecosystem delivers Insider Threat mitigation within every nut container in an independent way; the epitome of Zero Trust Data.
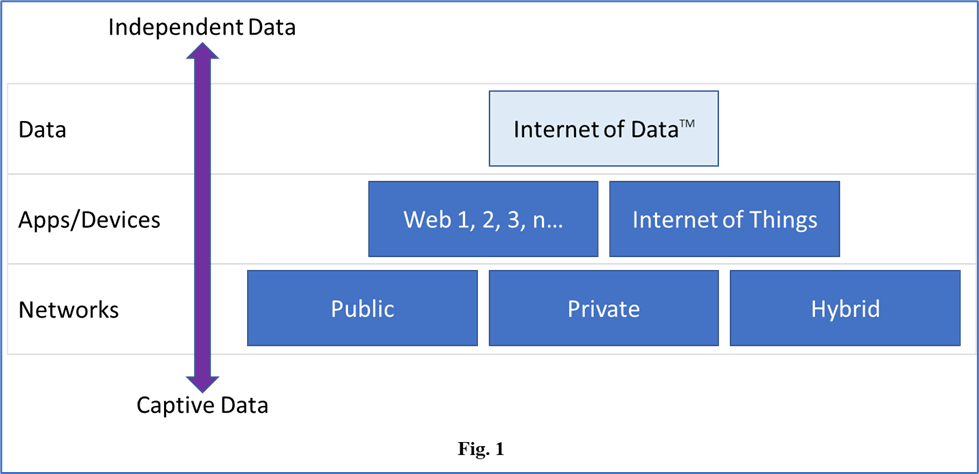
The Internet of Data establishes a new abstraction layer for the way we can interact with data and the way data can interact with other data (Fig. 1). IoD puts forth an environment where Operating Systems, File Systems and Networks are commoditized and your Data is prioritized.
In all honesty, does any user authenticate into a system for the pure pleasure of logging into a system? No, because, in the end, it’s all about the Data.